Over the past year, the conversations around Zero Trust have begun to accelerate. Much of the discussion is akin to data mesh and data fabric where business owners and management are hearing the term and asking what a Zero Trust product is. The term is also permeating data professionals’ conversations. This article provides a brief overview of Zero Trust and how data professionals can begin thinking about it.
What is Zero Trust?
Zero Trust is a security framework that is meant to enhance more traditional cyber security capabilities. There are many ways to design a Zero Trust Architecture and many products that can support the implementation. Zero Trust architecture allows an organization’ security posture to be more dynamic than the former practices of simply granting access or not granting access as a once-and-done operation. Zero trust looks continually at who, what, where, when any person or system is accessing the technical environment, whether that be at a network level or application level.
Consider this: the central focus for zero trust is managing user access. User access management is now incorporating fine grained data details about roles and attributes of those roles. Today, this functionality is coupled with automated scalable governance engines that can monitor length and breadth of access, immediately shut down access under predefined conditions, and provide regular analytics and reporting. The industry has moved from a simple username and password, to lengthy password phrases, password managers, multi factor authentication, and now, continuous authentication and identity access governance. This requires timely, sophisticated, well curated data!
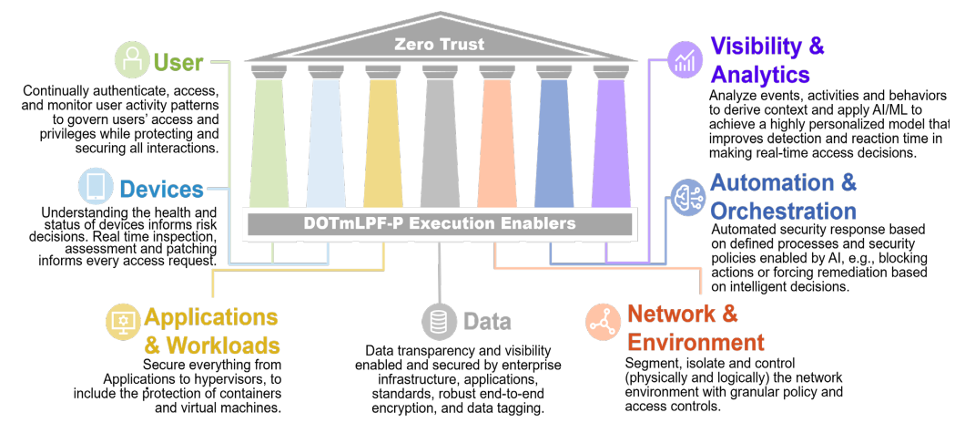
For reference, the Department of Defense (DoD) published a Zero Trust Strategy that demonstrates key pillars, as reflected in the figure below.
How Can Data Professionals Contribute?
Again, referencing the DoD Zero Trust pillars, note the data pillar. This pillar speaks to core data governance and data management practices. For Zero Trust architectures to be successful, they depend on scalable data governance and data management. Now there is an even greater, and immediate impact to our work!
As with many frameworks, it is advantageous to develop use cases and prioritize requirements. In your organization, you can talk to your security professionals to discuss the importance of good data practices to underpinning their Zero Trust initiatives. Take a few moments to educate them if they are not fully engaged and discuss data governance, tools, and impact. Incorporate the security team’s Zero Trust Initiative into your Data Governance and Data Management priorities. And always remember to let management know how you have contributed to protecting the integrity of the organization.
If you would like to learn more and hear a case study, join the Achieving Zero Trust Through Metadata session at the Enterprise Data World Conference on Wednesday September 20th, 2023 for the 2:45PM session. I’ll be speaking with my esteemed colleague Bonnie O’Neil who will also provide details on data cataloging automation offerings and techniques.
About the Authors
Shyla Kennedy is an experienced data professional and capability builder who has spent her career solving complex problems for large organizations. She has built and redesigned enterprise-wide data capabilities; incorporated emerging privacy practices into existing disciplines; managed ERP, and other cross-organizational software projects, and developed solutions to resolve multibillion-dollar accounting issues. She specializes in getting to the root of issues that are often at odds with pre-defined solutions.
She is currently a Lead Systems Engineer at MITRE Corporation. Her areas of expertise include data governance, data management, data privacy, business intelligence/analytics, accounting, finance, and program/project management.
Bonnie O’Neil is a well-known expert on all phases of data architecture, including data quality, business metadata, and governance. She is a regular speaker at many conferences and has also been a workshop leader at the EDW conference. In addition, she was the keynote speaker at a conference on Data Quality in South Africa.
She has been involved in strategic data management projects in both Fortune 500 companies and government agencies, and her expertise includes specialized skills such as descriptive analytics and semantic data integration. She is the author of four books, including “The Data Catalog: Sherlock Holmes Data Sleuthing for Analytics,” and over 50 articles and technical white papers.
Bonnie is a Principal Data Management Engineer at The MITRE Corporation.
Approved for Public Release; Distribution Unlimited. Public Release Case Number 23-2472
‘The author’s affiliation with The MITRE Corporation is provided for identification purposes only, and is not intended to convey or imply MITRE’s concurrence with, or support for, the positions, opinions, or viewpoints expressed by the author.’©2023 The MITRE Corporation. ALL RIGHTS RESERVED.