
The possibility for businesses to achieve efficiency, flexibility, and scalability is greatly enhanced by the fact that cloud computing technology is now available to all types of enterprises and marketplaces.
Many large businesses are still worried about the effectiveness of cloud computing on its own, and whether it can really replace their whole IT infrastructure. This is likely the reason that many businesses are thinking about using hybrid cloud infrastructure instead.
What is a Hybrid Cloud Environment?
Hybrid cloud environments integrate private cloud, on-premise, and public cloud services to allow organizations more freedom and choice to process information faster via cloud infrastructure.
When done correctly, it can potentially strengthen an organization’s security. The hybrid cloud helps businesses enhance their management efforts and scalability while simultaneously strengthening security and risk control.
Click to view larger
Another benefit provided by hybrid clouds for organizations is that they allow you to utilize your existing infrastructure. With useful tools like the UCaaS communication model, the cloud is sometimes depicted as an all-in solution, but that isn’t necessarily the case.
Businesses can still end up dumping valuable tech solutions in the name of cloud migration. Many are either bound by data center contracts or are saddled with amortizing hardware. Hybrid clouds offer ways of dealing with both.
Nonetheless, accepting and implementing hybrid cloud infrastructure has its unique issues that call for preparation and a reevaluation of security guidelines and practices. Every company trying to reduce security risks while maximizing the advantages of hybrid clouds should place cloud security at the top of their priority list.
What Are the Components of Hybrid Cloud Security?
Physical, technological, and administrative security levels are all necessary for the hybrid cloud.
Physical Protection
Physical security is the responsibility of the vendor for your public cloud components. Your internal infrastructure (private cloud) should be secured with reliable locks, cameras, restricted physical access, and a regulated environment.
Don’t ignore potential damage caused by temperature, humidity, and water leaks.
Technical Protection
To provide effective data security and avoid data breaches, several security policies and safeguards must be in place.
Data in transit requires a different kind of encryption compared to data at rest. Make sure that the network session encryption is sufficient for data in transit. Use hardware and whole disc encryption for data that is at rest.
Employ virtual private networks (VPNs) to secure communications between elements operating in separate settings.
Use change monitoring, role-based access management, endpoint protection, dependable data backups, and multi-factor authentication as further security measures.
Administrative Protection
Administrative security requires written policies and guidelines like processes for evaluating risks, disaster recovery strategies, policies for data protection, and employee education.
Common Hybrid Cloud Challenges and How to Resolve Them
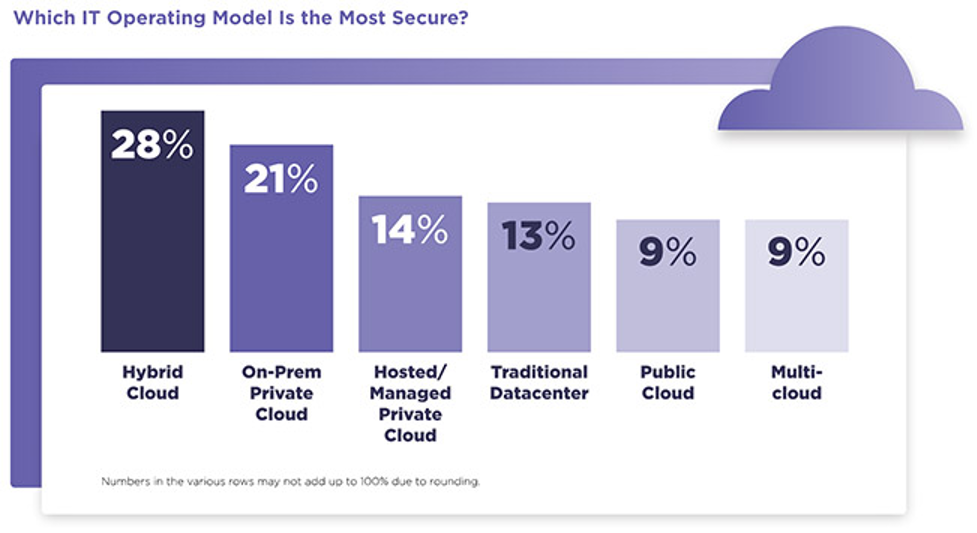
Hybrid cloud environments are regarded as the safest cloud deployment choice by IT experts all over the world. Over 28% of them chose the hybrid cloud as their preferred IT operating infrastructure.
Click to view larger
However, a hybrid system made up of combined private and public cloud services has several security concerns that are exclusive to it:
Poor Designation of Responsibility
Poor cloud provider communication and poorly defined service-level agreements (SLAs) can make it difficult to resolve conflicts or respond to security breaches, and raise doubts about who is to blame for outages or other issues.
You can designate workloads to particular areas of the hybrid cloud to prevent this. There should be a separate outage and incident strategy, as well as unique performance and security controls for each workload.
Security and Governance Issues
Each public and private cloud service offers distinct privacy and security features. Loss of control and visibility may come from the transfer of data between them.
Make sure that the proper security procedures are used for all internal systems as well as private and public cloud services to overcome this problem. Establish clear roles and expectations with your cloud provider in terms of security governance.
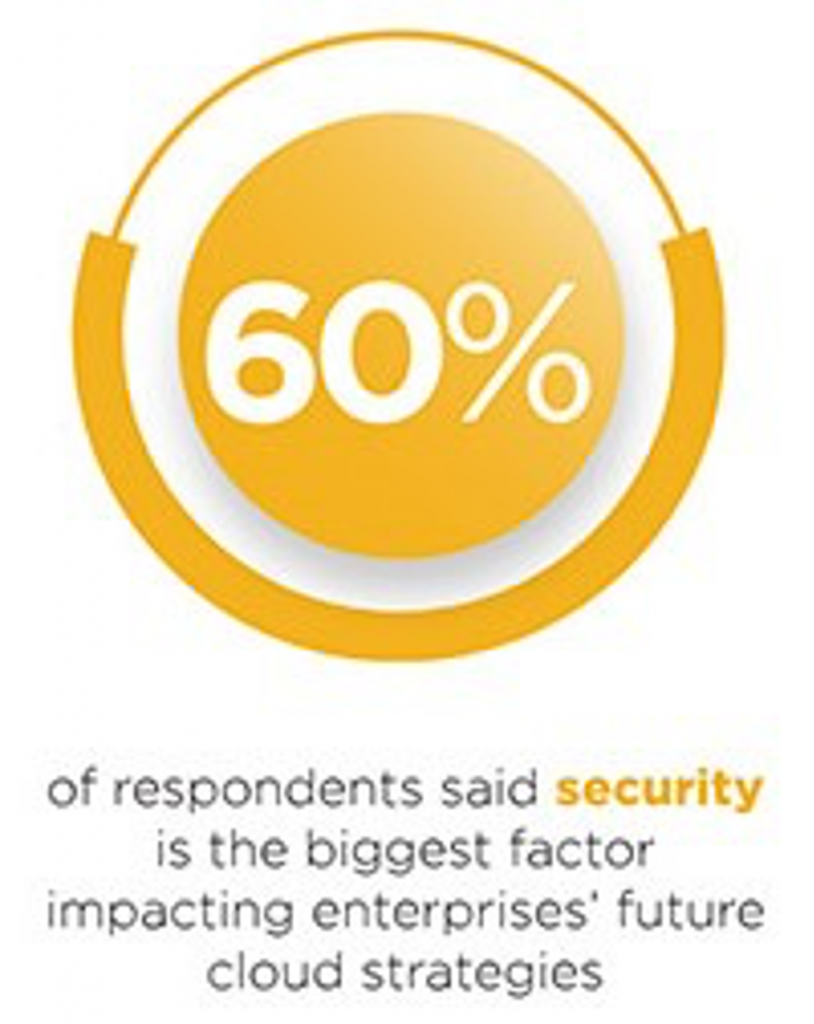
The recognition of security as a crucial component of future cloud strategies for businesses is becoming more widespread.
Click to view larger
Keep a close eye on any activities surrounding the data you keep in private and public clouds. Ensure that you and your cloud provider promptly share information about any issues.
Legal and Compliance Risk
Compliance and regulatory issues may arise when sensitive material is freely transferred between public and private venues.
Even minor violations of rules and regulations can result in severe penalties or even legal action in closely regulated industries like governance, healthcare, and finance.
Regulation compliance for private and public cloud services must be handled by your business. You are responsible for ensuring that your cloud provider has put all essential procedures and safeguards in place to protect your data.
Additionally, you must ensure that your internal controls adhere to the rules you are required to follow. To maintain total control over their sensitive data, several businesses opt to exclusively store it in private clouds.
Managing Security-Related Incidents
Both you, the customer, and the public cloud service provider are accountable for identifying, documenting, and handling security breaches. To get prompt notification of a breach, keep lines of communication open and establish clear notification guidelines.
Managing Access
Hybrid cloud storage infrastructure may be at risk of security breaches if there are multiple access points. To ensure security rules and best practices are strictly implemented you should always be aware of who has access.
Vulnerability of Shared Cloud Infrastructure
Public cloud computing often means sharing resources and multi-tenancy arrangements. Attackers in a hybrid cloud can worm their way into your private cloud system and on-premises infrastructure via the public cloud.
To help prevent this, implement strategies like digital device authentication and multi-factor authentication to strengthen who can access your systems.
Audit and Visibility
It can be challenging to monitor activities such as data mining across both public and private cloud systems. Utilize tools that let you audit every cloud system from a single location.
Best Practices for Hybrid Cloud Security
Though embracing a hybrid cloud environment can be challenging, keeping in mind these best practices can help businesses adopt it as smoothly and securely as possible.
Security and Interoperability
A company typically has to integrate both new and existing technologies when creating a hybrid cloud strategy.
Nevertheless, integrating these components into a hybrid cloud presents crucial issues regarding how cloud solutions complement existing ones and how to set up the system and its constituent elements safely.
You must start thinking about these issues from the beginning of the architectural process to address them. Get access to experts who can respond to these complications and provide support.
By doing so, you can seamlessly execute the hybrid cloud approach, satisfying both business and data governance objectives.
Automation
Security monitoring has to expand along with infrastructure expansion into cloud systems like a cloud data warehouse.
Manual processes for assessing and contextualizing security data scale poorly with hybrid clouds because they end up being asynchronous, which can affect data breach response. This makes it difficult to spot irregularities early enough to prevent damage.
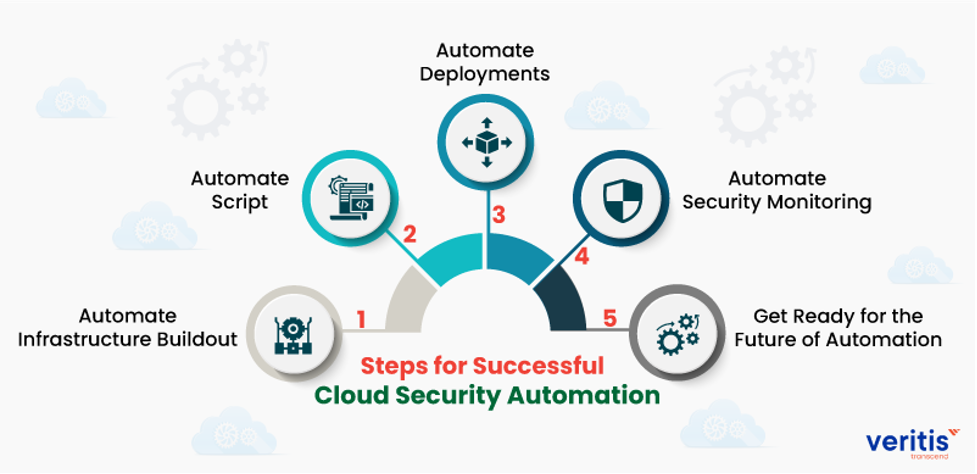
Security automation has a significant positive impact on hybrid cloud infrastructures.
Click to view larger
Tech solutions such as business VoIP must be set up to generate the necessary security data and logs. To gather that data, process it, and achieve timely threat identification, a central system must be created.
Data Security Concerns
Encryption of data in transit and at rest is required by current data security legislation as well as security best practices.
Any hybrid cloud plan must take the company’s complicated data processing requirements into account as data and services are split between on-premise and cloud infrastructure.
Additionally, a plan for reliable connectivity between on-premises and cloud infrastructure should be included.
Securing Your Future
Due to the several advantages we have covered above, the hybrid cloud is gaining ground as the preferred option for many businesses that prioritize cybersecurity. Hybrid cloud security, however, has several issues, some of which are more pressing than others, much like any other network type.
However, you can overcome these difficulties if you have competent staff, a reputable cloud provider, and apply solid data protection and security procedures. Furthermore, when dealing with elaborate IT infrastructures, there is no single solution that suits all circumstances or meets the requirements of all businesses.
To safeguard your sensitive data, it is crucial to understand your business needs and address them accordingly.
