
Several years ago, while working for a firm developing groundbreaking software, I proposed to my boss that we were, in fact, creating an entirely new market class of software. My boss quickly dismissed this notion, stating that software firms don’t create market categories — analyst firms do. Fast forward to today, and those very analyst firms have defined two critical categories: Data Security Governance (DSG) and Data Security Posture Management (DSPM). In this author’s opinion, these categories form the perfect combination, much like a Reese’s Peanut Butter Cup, for data governance and security professionals. In this article, I’ll explain why this fusion is essential for the future of defensive data governance.
What Is Data Security Posture Management?
Data Security Posture Management (DSPM) is a set of technologies that empower organizations to discover, categorize, and manage structured and unstructured data across cloud service platforms. As data flows through complex pipelines and crosses geographic boundaries, DSPM allows governance, security, and risk management leaders to identify and take steps to mitigate security and privacy risks that are contained within.
The need for DSPM is driven by the rapid expansion of data across global cloud service platforms. This fact has created an urgent need to uncover and manage underutilized or previously unknown data repositories. This need has become even more pressing following a recent SEC ruling that mandates prompt reporting of material cybersecurity incidents, compelling organizations to swiftly determine materiality and disclose these incidents.
Core capabilities of DSPM include building comprehensive data maps and pipelines, analyzing data lineage and access, identifying data risks, and generating alerts. These functions enable enhanced monitoring for indicators of compromise, vulnerabilities, and misconfigurations that could lead to data breaches or privacy incidents. Additionally, DSPM accelerates the evaluation of how data security policies should be enforced across siloed security controls, ensuring a more coherent and unified approach to data protection.
However, while DSPM provides governance and security personnel with the tools to assess access privileges and enforce the principle of least privilege, it stops short of systematically controlling the risks it identifies. This limitation underscores the need for a broader strategy that integrates DSPM insights with active risk management measures to ensure vulnerabilities are uncovered and mitigated.
What Is Data Security Governance?
Data Security Governance (DSG) integrates data security controls with business logic and fine-grained authorization, leading to significant improvements in data protection and overall efficacy of managing security and access. Truth be told, many organizations struggle with outdated policies, obsolete tools, and silo-specific security controls that make consistent data security practices difficult to implement across the board. A fragmented approach often focuses narrowly on detecting attackers, leaving broader security governance challenges unaddressed.
Managing security and access permissions in large data repositories has traditionally been a cumbersome task, often resulting in a maze of complex access rules and security measures. DSG streamlines this process by automating the enforcement of policies through role-based access control (RBAC) and attribute-based access control (ABAC), ensuring permissions are precisely aligned with both the user’s identity and the specific content of the data. Additionally, with the ability to also apply global controls, DSG not only simplifies the management of data security, but also enhances compliance with regulatory requirements.
By applying posture data, organizations can achieve better data security observability and more robust compliance, thanks to the centralized systems that DSG offers for policy and permission control. These systems prevent the exponential growth of data access rules by delivering the essential components required for good data governance and optimized security controls, ensuring that data remains secure while access is properly managed and regulated.
Why Better Together
A complete data security platform combines data discovery, policy definition, and enforcement across data silos, creating an end-to-end solution that addresses the critical needs of modern data governance and security. By integrating these functions, the platform prevents the exponential growth of data access and policy rules, ensuring that organizations maintain control over their data without becoming overwhelmed by complexity. Gartner identifies this approach as a
“Data Security Platform.”
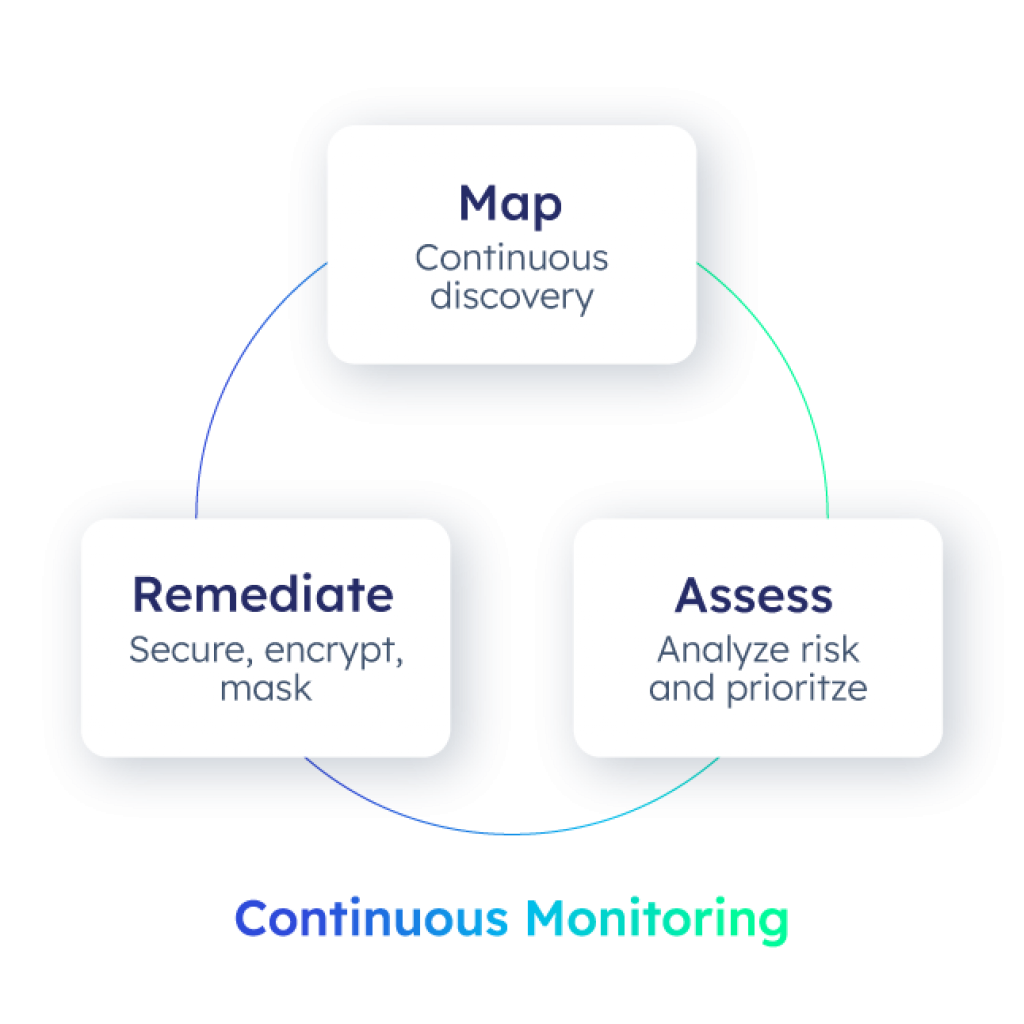
This platform essentially transforms DSPM into an active system that not only maps and assesses data security, but also automates remediation. The mapping process involves enterprise-grade sensitive data discovery, classification, and tagging across both structured and unstructured data. This enables the visualization of the sensitive data posture, showing the location of sensitive information, who has access to it, who is actively accessing it, and the associated business risks.
The platform goes further by assessing the risk impact of the data security posture. It analyzes over-provisioning, creates risk-based scores, and identifies risky access patterns, providing organizations with a clear understanding of potential vulnerabilities. To address these risks, the platform then automates compliance workflows that fine-tune data access controls, such as role-based, attribute-based, and time-based access controls (RBAC, ABAC, TBAC), along with masking and encryption. This creates a comprehensive approach shown below for ensuring that data remains secure while access is tightly controlled and continuously optimized.
Parting Words
In this article, I have explored the integration of DSPM and DSG into a comprehensive data security platform that combines data discovery, policy definition, and enforcement across data silos. By transforming DSPM into an active system, this platform delivers an end-to-end solution that maps, assesses, and remediates data security risks, offering enterprise-grade sensitive data discovery, risk assessment, and automated compliance workflows. This approach enables organizations to streamline data access controls, enhance data security observability, and maintain regulatory compliance, all while preventing the exponential increase of data access and policy rules. This should be the aim of data governance and security personnel, systematize and make the entire process simpler.
