
It’s past time for a comprehensive data security strategy
Information Security professionals tend to focus on network, cloud, application, and IoT security along with perimeter defense. These are essential and provide a high degree of protection for systems and files. But what happens when your defenses are breached by a phishing attack and user credentials for data and analytic systems are compromised? Or, if the attack is internal and involves unauthorized access of sensitive data? These scenarios are just a couple reasons why you need a Comprehensive Data Security Strategy. In practice, it may be your last line of defense.
The good news is executive-level commitment to a broad data governance strategy, which in theory should include Data Security, is quickly gaining momentum across industries in the world of data and analytics. This commitment is matched with real action and investments. In a recent Gartner survey, 78% of CFOs said they will increase or maintain enterprise digital investments. And a Gartner forecast states worldwide IT spending will grow 3% in 2022.
Above, we said “in theory.” In many cases, the reality is a comprehensive data security strategy is not included in governance initiatives. Why? Because everyone assumes someone else is taking care of it. (Not be juvenile, but we’re reminded of the grammar school adage: “When you assume, you make an ass out of u and me.”) Today, data security is implemented in silos, which inevitably leads to significant security gaps and inconsistent implementation. And more times than not, no one is “owning” the holistic enterprise data security strategy. In addition, organizations face challenges from three primary sources:
- Technology: One look at the Andreessen-Horowitz blueprints for the modern data infrastructure (see Fig. 1) and it’s obvious that the abundance of data storage, compute, and processing options is responsible for creating the complexity that’s become a nightmare to manage. Even more daunting is the ability to properly secure this plethora of data platform choices, so that our data democratization success does not run afoul of data security and data privacy mandates.
- People: Ten years ago, data protection was the purview of a limited number of very skilled individuals managing data end-to-end or security experts who typically reported to an IT function. Today, business ranks are filled with those same skills and expertise with Data Stewards, Data Analysts, and Data Scientists tasked to build in data governance, while CISOs, CIOs, and CDOs focus on compliance requirements, implementation, and how to best exploit data.
- Processes: In just a few short years, the center of gravity for information technology has migrated from on-premises to the cloud, and along with it, a stream of new regulations to protect and satisfy consumer privacy. This has driven demand for new processes to regulate and ensure the responsible discovery, access, and use of data. All of these factors have compelled organizations to adopt processes that support a scalable approach to data security and governance.
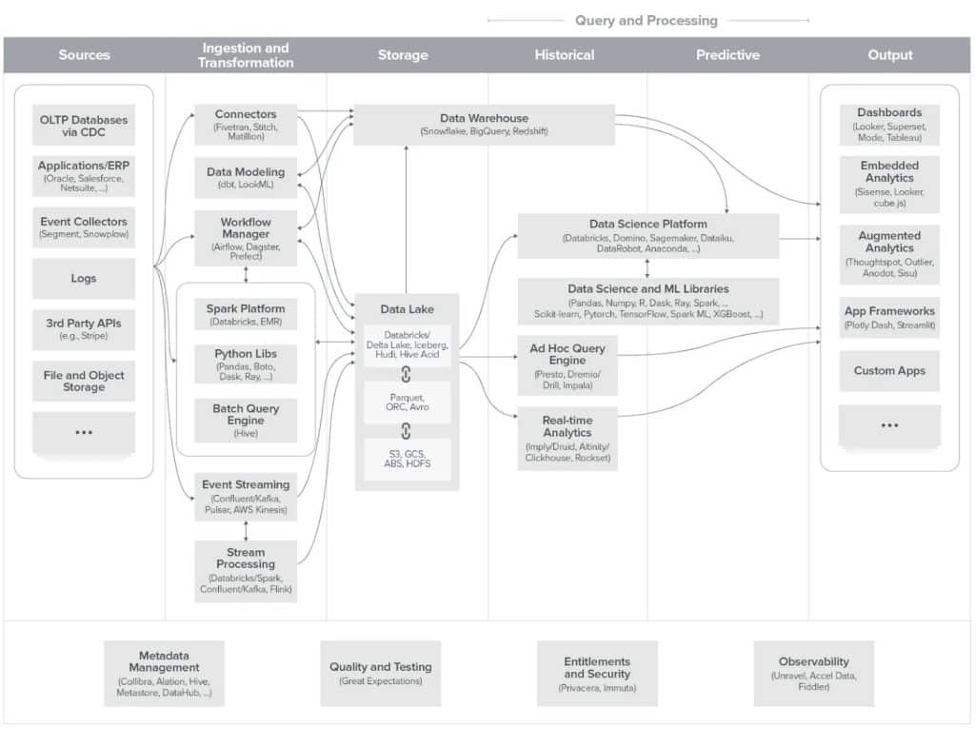
Click to view larger.
The Increasing Cost Of Failure
While the investment required to establish a comprehensive approach to data protection may be substantial, the cost of doing nothing or getting it wrong will be endlessly painful.
- Globally, the average cost of a security breach in 2022 is $4.35M, compared to $3.8M two years ago. In the United States, that number is a whopping $9.44M. Inconsistent and mis-configuration of data services on average cost $4.14m per incident.
- Fines for ignoring or violating regulations like GDPR are enough to significantly derail operations, with companies like Amazon and WhatsApp reporting fines in the hundreds of millions of dollars.
- Data analyst, data engineering, and data science productivity remain a major challenge, as 80% of their time is spent on finding and getting access to the right data as well as cleaning that data.
If you have 1,000 analysts, each losing the equivalent of 4-5 hours per year (estimate $500), this equates to $500,000 or more wasted just on analyst productivity.
- Though not always immediately tangible, the cost of delayed business decisions due to project inertia is inevitably, painfully tangible down the road.
- The financial impact associated with data breaches, damage to company brand, and subsequent loss of consumer confidence can negatively impact an enterprise for years.
How to Succeed? Modernize Your Data Security Governance Thinking.
Modernization starts with thinking differently about your Technology, People, and Process challenges and approaches.
- Modernize data security governance technology: A key point illustrated by the Andreessen-Horowitz framework is data security and data governance must exist across every part of the data journey and data lifecycle— from data discovery, data ingestion, data transformation, and data storage to data visualization. Maintaining that data security and privacy posture on a point-by-point basis is simply not viable.
Advice: Implement a comprehensive data security platform that provides a unified control plane across your entire hybrid data estate.
- Modernize the roles of your data stakeholders: Data security is becoming well within the purview of the CISO. We’re starting to see evidence that strategy ownership is being placed within the CISO team. But a successful strategy will also require inclusion of other key stakeholders. Data stakeholders have expanded beyond the traditional experts employed by IT. Today, our best data experts live in the business. But while we have embraced the data analyst or data scientist embedded in the business team, we have yet to formally recognize data governance stakeholders in the same way. The data champions and data owners are business people.
Advice: Formalize security and data governance objectives early on. Empower your business data stakeholders to achieve objectives in a scalable and automated manner.
- Modernize your data governance processes: Embarking on the first two steps essentially guarantees you’re on the road to this third critical element. Gartner speaks extensively of the evolution of data governance from a Dictated process (IT command and control) to a Distributed process (everything left to be performed at the edges of the process).
Advice: Implement a blended model where the system is based on federated responsibilities that includes some degree of centralized control and auditability.
Closing Thoughts on Opening Your Mind to Modernization
The world of data processing is exploding with new specialized data processing startups being born seemingly on a daily basis. AWS, Snowflake, Databricks, Azure, and Google continue their rapid growth, delivering more choices within their ecosystems, while increasing their complexity to enforce security and privacy across a diverse landscape. The only way to future-proof your analytics along with your security and privacy posture is through Unified Data Security Governance. Privacera is built on open-source Apache Ranger, the de facto standard for enabling, monitoring, and managing comprehensive data security across the Hadoop platform. Read more about how Apache Ranger has evolved beyond Hadoop to become the open-standard choice for vendors like Starburst, Ahana, and many others.
